Difference between revisions of "Security Strategy"
(→Overview) |
(→Lingoport Suite Components) |
||
| Line 15: | Line 15: | ||
For more details on any of these, please see [[Lingoport Security Overview]]. |
For more details on any of these, please see [[Lingoport Security Overview]]. |
||
| + | |||
| − | ==Lingoport Suite Components== |
||
| − | + | == Typical Deployment of the Lingoport Suite and Ports == |
|
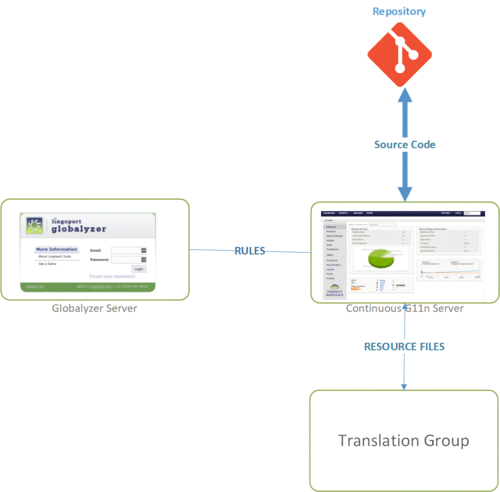
| + | Setting up the Suite on a Customer's system can be done in many ways, as shown in the different deployment scenarios. The following is meant to show the necessary access to the system. |
||
| + | |||
| + | |||
| + | * The code repository needs to be able to work with the Continuous Globalization Server. This is done through the Jenkins jobs and Lingobot. |
||
| + | * The Continuous Globalization Server needs to be able to access the Globalyzer rulesets that are located either on our hosted server or on a local server. |
||
| + | * The Continuous Globalization Server needs to be able to send and receive resource files with the Translation Management System. |
||
| + | ** The resource files are also stored in the code repository. |
||
| + | * Additionally, there are administrative needs for Continuous Globalization Server to be able to access Jenkins plugins, SMTP email, and SSH access. |
||
| + | |||
| + | [[File:Deployment - Wiki.gif|500px]] |
||
| + | |||
| + | = Ports = |
||
| + | * Jenkins is accessed via |
||
| + | ** port 80 or 443 |
||
| + | ** port 8080 if installed prior to May 2018 |
||
| + | * Lingoport Dashboard is accessed via |
||
| + | ** port 80 or 443 |
||
| + | ** port 9000 if installed prior to May 2018 |
||
| + | * The Translation Vendor may be accessed by different means, for instance |
||
| + | ** port 21 for FTP or |
||
| + | ** port 22 for SFTP. |
||
| + | ** Other ports for different vendors |
||
| + | * Access for the Lingoport (or internal) installation team is typically done over SSH / via PuTTY. |
||
| + | ** Alternately, it may be done through GoToMeeting/Webex screensharing between a Lingoport engineer and a customer engineer. This process may be significantly slower. |
||
| + | * The system must be able to access https://www.globalyzer.com. |
||
| + | |||
| + | = Other aspects = |
||
| + | * Jenkins installation requires access to the Jenkins update site, http://updates.jenkins-ci.org |
||
| + | * Dashboard may require access to the SonarQube update site, http://update.sonarsource.org |
||
| + | * Notifications are sent using an SMTP account: The system must allow access to an SMTP server (e.g. smtp.gmail.com for Google) |
||
| + | |||
*[[Lingoport Suite Product Security]] |
*[[Lingoport Suite Product Security]] |
||
**[https://wiki.jenkins.io/display/JENKINS/Securing+Jenkins Securing Jenkins] |
**[https://wiki.jenkins.io/display/JENKINS/Securing+Jenkins Securing Jenkins] |
||
Revision as of 18:23, 9 December 2019
Contents
Overview
Lingoport works to provide customers with a reliable service that safeguards private information. We implement various security-centric policies in support of these principles. Lingoport’s security standards have been built to support the security conscious, including customers in industries such as Human Resources, Finance, and Medical Systems.
- We protect our organization, and our customers, by addressing Key Security Principles
- We consider security Throughout Our Organization.
- We take customer security very seriously during Service Projects.
- We minimize security exposure to our customers through Security Conscious Product Design.
- We adhere to standard security practices in our cloud hosted environments. Security and Cloud Offerings
For more details on any of these, please see Lingoport Security Overview.
Typical Deployment of the Lingoport Suite and Ports
Setting up the Suite on a Customer's system can be done in many ways, as shown in the different deployment scenarios. The following is meant to show the necessary access to the system.
- The code repository needs to be able to work with the Continuous Globalization Server. This is done through the Jenkins jobs and Lingobot.
- The Continuous Globalization Server needs to be able to access the Globalyzer rulesets that are located either on our hosted server or on a local server.
- The Continuous Globalization Server needs to be able to send and receive resource files with the Translation Management System.
- The resource files are also stored in the code repository.
- Additionally, there are administrative needs for Continuous Globalization Server to be able to access Jenkins plugins, SMTP email, and SSH access.
Ports
- Jenkins is accessed via
- port 80 or 443
- port 8080 if installed prior to May 2018
- Lingoport Dashboard is accessed via
- port 80 or 443
- port 9000 if installed prior to May 2018
- The Translation Vendor may be accessed by different means, for instance
- port 21 for FTP or
- port 22 for SFTP.
- Other ports for different vendors
- Access for the Lingoport (or internal) installation team is typically done over SSH / via PuTTY.
- Alternately, it may be done through GoToMeeting/Webex screensharing between a Lingoport engineer and a customer engineer. This process may be significantly slower.
- The system must be able to access https://www.globalyzer.com.
Other aspects
- Jenkins installation requires access to the Jenkins update site, http://updates.jenkins-ci.org
- Dashboard may require access to the SonarQube update site, http://update.sonarsource.org
- Notifications are sent using an SMTP account: The system must allow access to an SMTP server (e.g. smtp.gmail.com for Google)
Lingoport Virtual Machine
More...
Should we have something that talks about the security enhancements that we have in our products or is this already in these pages?
Several security enhancements have been implemented for the Globalyzer Server. Our password encryption algorithm has been upgraded to use bcrypt, forgot password now performs a password reset rather than retrieval, and we now guard against clickjacking and directory/path traversal attacks. Our version of Tomcat has been upgraded to enable some of these security features.
FAQ
Can other customers see our rulesets and information on Globalyzer.com ?
How often is security testing done on the code or the systems?
Is data transferred between the customer and the Continuous Globalization System securely? What about between the Continuous Globalization System and the translation vendors?
How do you document security for third-party applications?
For Services customers, how do you ensure that the code and company information is secure?
How are security issues and concerns handled within the company?
How does Lingoport monitor an AWS VM for security issues ( logins, invalid logins, data transfers, etc)?
Has Lingoport had any security breaches?
Please send any security inquiries or reports to either support@lingoport.com or security@lingoport.com.
Globalyzer supports the additional security of HTTPS for all data that passes between the Client and the globalyzer.com Server.
L10n Vendor Lingoport FTP Protocol: FTP supports SSH and SSL encryption; The FTP system can allow only some IP ranges to access the FTP port(s)
Machine Learning: to use Machine Learning, you must install H2O.ai to your system. It's an in-memory platform so you don't need to worry about the security of your code and data.
LDAP and security.