GitHub Pull Requests
Contents
GitHub
GitHub is a Web-based Git repository hosting service. It offers all of the distributed revision control and source code management (SCM) functionality of Git as well as adding its own features.
Git Pull Requests
Files can be committed in a Git branch or directly in Master. When committing files in a branch, pull requests let you know what changes you've made to a repository before they are committed to the repository's master branch. Once a pull request is sent, interested parties can review the set of changes, discuss potential modifications, and even push follow-up commits if necessary.
You can configure Globalyzer to scan the files that changed between the two branches of the pull request, and post a Globalyzer Analysis Summary on the pull request in Github.
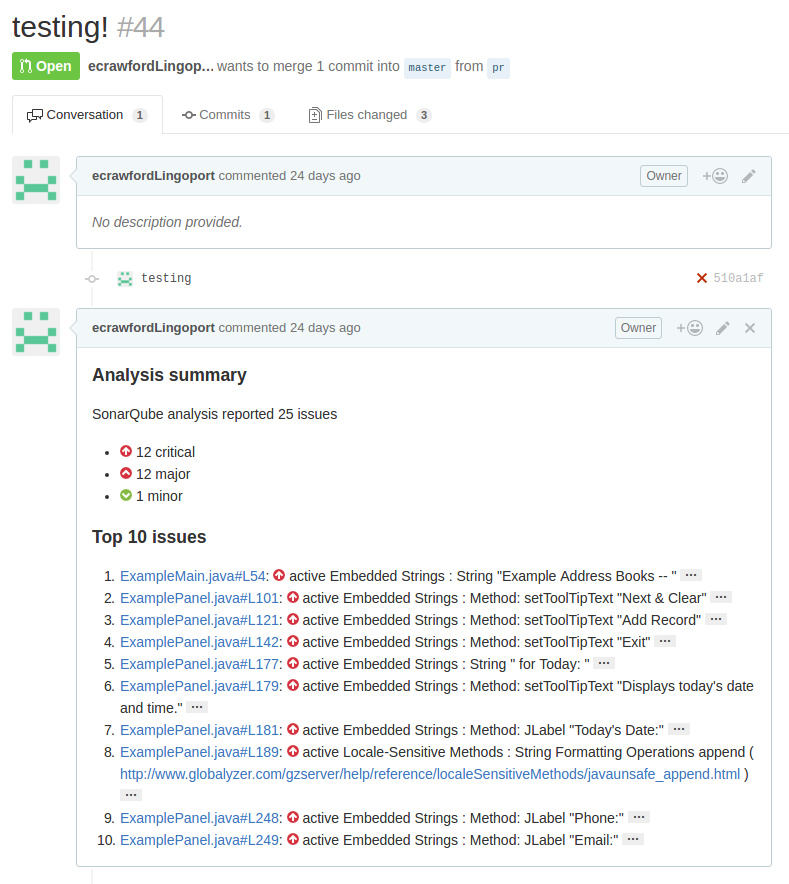
Example of a Pull Request Analyzed with Globalyzer
This is pull request #44. The change to the code in the pull request was to add multiple embedded strings and a locale-sensitive method to the files ExampleMain.java & ExamplePanel.java. This pull request is reporting 25 different issues, however since the sonar-project.properties attribute is set to sonar.github.disableInlineComments=true, the top ten issues (sorted by severity, by component, then by line) are put into a summary analysis as a pull request comment.
Globalyzer analysis flagged these lines as critical issues. Clicking on the link next to the issue number will send the user to the line of code in that respective file.
Before merging the code back to master, the developer would typically externalize these strings, fix the locale-sensitive method issue, and re-submit the changed code / resource files for further analysis.
Pull Request Analysis Configuration
Configure github.properties
You must create the file /var/lib/jenkins/Lingoport_Data/Dashboard/github.properties with the following contents:
- github.login=<your github login>
- github.oauth=<your github token>
To create a token for yourself on Github:
- browse to https://github.com
- select Settings from login dropdown
- select Developer Settings on left
- select Personal access tokens
- click Generate new token
- fill out token information
- click Generate token
Create a Pull Request Jenkins Job for Your Github Repository
Create a new Jenkins job named <YourRepo>-PullRequest by copying the existing job RepoName-PullRequest.
You do not need to configure this job, just create it.
Create Web Hook for Github Repository
Globalyzer Dashboard uses the SonarQube sonar-project.properties file for configuration. This file should be in your repositories base directory. For the i18n analysis of the pull request, the sonar-project.properties file needs the following attributes:
sonar.analysis.mode=preview- It is imperative this attribute is set to preview to work. If not set, it defaults to publish mode, and could create future issues for analysis on this pull request.
sonar.github.login=- Your GitHub login name
sonar.github.oauth=- GitHub oauth is your unique GitHub personal access token: created @ https://github.com/settings/tokens
sonar.github.repository=- The repository you are working in. If repository link is https://github.com/ursulaLingoport/indexing2, this attribute should be set to
sonar.github.repository=ursulaLingoport/indexing2
- The repository you are working in. If repository link is https://github.com/ursulaLingoport/indexing2, this attribute should be set to
sonar.github.pullRequest=- The number of the pull request you plan to run an i18n analysis on.
sonar.github.disableInlineComments=- If set to true (highly recommended), issues will not be reported as inline comments but only in the global analysis summary in sorted order. False by default.
- This Wiki page is based around this attribute being set to true. Here is an example of a Pull Request when this attribute is set to false (issues appear as individual inline comments within the pull request).
GitHub Personal Access Token Security
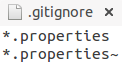
Since the sonar-project.properties file includes a personal access token (OAuth), this file cannot be pushed to a remote repository. This exposes the users personal access token to the public, and therefore will void the token. If this happens, you should receive an email from GitHub acknowledging the user of the exposure and the token's decommission. In order to avoid this, the user must avoid staging the sonar-project.properties file for commit. In order to do this, you can create a .gitignore file in your repository's root directory to ignore all files with the .properties extension. It is recommended to do this in your master branch, so all forked and branched repositories will not face this issue.
Here is an example .gitignore file that will prevent this issue from occurring:
GitHub WebHook
The Pull Request on GitHub needs to trigger a Web hook back to Lingoport's Jenkins instance. To do so:
- Navigate to the GitHub repository as an Admin account
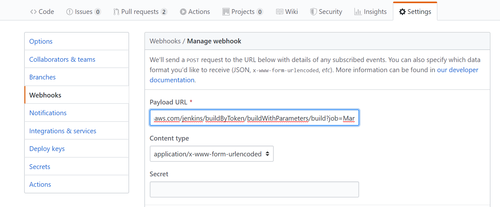
- In Settings tab for the GitHub repository (available if the account has Admin permissions), add a Webhook
- The Web hook should follow this pattern:
Payload URL: http(s)://JENKINS_URL/jenkins/buildByToken/buildWithParameters/build?job=RepoName-PullRequest&token=HOOK
Content type: application/x-www-form-urlencoded
Pull Request event selected
Active
For example:
- Test the Web hook and especially check for firewall issues going back to the Jenkins system