Difference between revisions of "AWS Security"
(→The Customer Network without the Lingoport Suite) |
|||
| (13 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | Deploying the Lingoport Dedicated VM using AWS has many security advantages. This section develops some of the layers starting with a customer's network to the full implementation of the dedicated VM accessing the customer's network Git repositories. |
+ | Deploying the Lingoport Dedicated Virtual Machine (VM) using AWS (https://aws.amazon.com/what-is-aws/) has many security advantages. This section develops some of the layers starting with a customer's network to the full implementation of the dedicated VM accessing the customer's network Git repositories. |
== The Customer Network without the Lingoport Suite == |
== The Customer Network without the Lingoport Suite == |
||
| − | [[File:AWS Security 1.PNG| |
+ | [[File:AWS Security 1.PNG|500px]] |
| + | |||
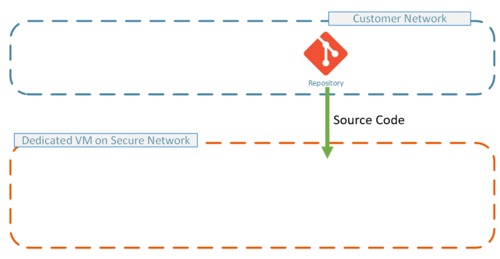
| + | The customer network before any Lingoport dedicated VM. It is expected to be a secure environment. The code repository is in the secure environment. |
||
== The Lingoport Dedicated VM Restricted Access to the Repository == |
== The Lingoport Dedicated VM Restricted Access to the Repository == |
||
| + | [[File:AWS Security 2.PNG|500px]] |
||
| + | |||
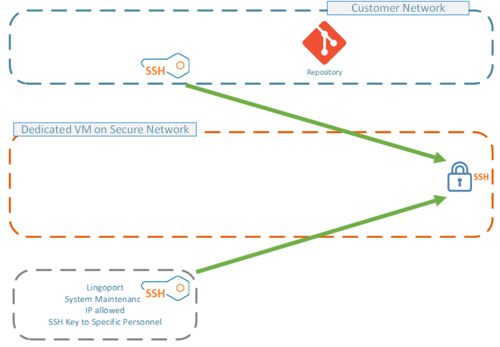
| + | The first step in this deployment is to instantiate an AWS VM. The Customer IT adds only that VM to the list of specific IP's which can access the repositories. The only access provided is to version control systems such as Git (GitHub, Bitbucket, Gitlabs), TFS, or Subversion. |
||
| + | |||
| + | No customer data or systems (credit card information, live databases, client data, etc.) are granted access to the Lingoport Dedicated VM. |
||
== Restricted Access to the Lingoport Dedicated VM == |
== Restricted Access to the Lingoport Dedicated VM == |
||
| + | |||
| + | [[File:AWS Security 3.PNG|500px]] |
||
| + | |||
| + | Conversely, only a restricted set of IP's are allowed to access the Lingoport Dedicated VM. For instance, a system has to be either in the Customer's network or in the Lingoport network to be granted access to the Lingoport Dedicated VM. |
||
| + | It behaves as an extension of the customer's network. No other party can gain access to the Lingoport Dedicated VM. |
||
| + | |||
| + | Furthermore, access to the AWS Lingoport Dedicated VM is restricted by SSH key. A public key needs to be set on the Dedicated VM to access connections. |
||
== HTTPS and IP Restrictions to the Lingoport Applications == |
== HTTPS and IP Restrictions to the Lingoport Applications == |
||
| + | [[File:AWS Security 4.PNG|500px]] |
||
| + | |||
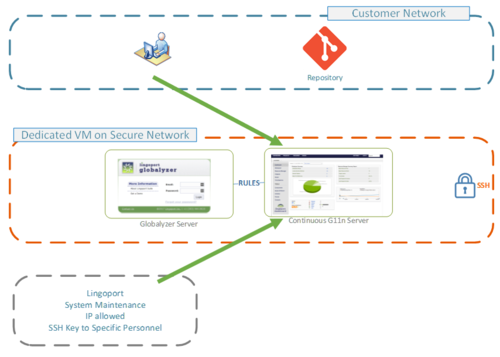
| + | The application on the AWS Lingoport Dedicated VM (the Dashboard or Jenkins) is only accessible when the following conditions are met: |
||
| + | |||
| + | The IP of the calling system is granted access, typically: |
||
| + | * Customer IP range |
||
| + | * Lingoport IP range |
||
| + | |||
| + | The application is secured by account and password over HTTPS. |
||
| + | |||
| + | In other words: |
||
| + | |||
| + | * No one outside the authorized range can reach the system |
||
| + | * Only authorized accounts access / see the Dashboard |
||
| + | * Data communication is over HTTPS |
||
== Secure Transfer of Resource Files to/from Translation == |
== Secure Transfer of Resource Files to/from Translation == |
||
| + | [[File:AWS Security 5.PNG|500px]] |
||
| + | |||
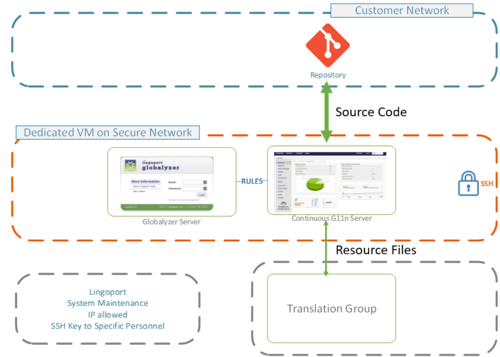
| + | The AWS Lingoport Dedicated VM has code obtained from the repositories on the customer's version control system. A few files, those which require translations, need to be sent to a translation group (See Language Service Providers, TMS, etc.). Those application files are called 'Resource Files'. They are not the code of the application, they are the user visible strings. The resource files are typically .properties, .json, .resx, etc. They are not .java, .js, .c#, etc. |
||
| + | |||
| + | Most commonly, in order to secure the send the resource files to and from the translation group, the files transfer over Secure FTP: |
||
| + | * LRM (Lingoport automation) deposits the files on an SFTP endpoint |
||
| + | * The Translation group retrieves the files. They are not on the SFTP any longer |
||
| + | * The Translation group pushes the translated files to another SFTP endpoint. |
||
| + | * LRM (Lingoport automation) retrieves the files from that end point. The files are not the SFTP any longer. |
||
| + | |||
| + | Transfer security: |
||
| + | * The protocol used is Secure FTP (SFTP). Or with specifical allowance and request FTPS. |
||
| + | * The SFTP/FTPS server only allows the minimum IP range necessary: |
||
| + | ** Dedicated VM IP range |
||
| + | ** Translation Group IP range |
||
| + | ** The protocol is SSH (SFTP - Recommended) or SSL (FTPS - as a fallback where specifically requested). |
||
| + | |||
| + | For specific translation vendors, direct connections to the vendor API point may be substituted for SFTP. These connections are encrypted over HTTPS(TLSv1.2), using an api token to authenticate. |
||
Latest revision as of 20:08, 11 February 2021
Deploying the Lingoport Dedicated Virtual Machine (VM) using AWS (https://aws.amazon.com/what-is-aws/) has many security advantages. This section develops some of the layers starting with a customer's network to the full implementation of the dedicated VM accessing the customer's network Git repositories.
Contents
The Customer Network without the Lingoport Suite
The customer network before any Lingoport dedicated VM. It is expected to be a secure environment. The code repository is in the secure environment.
The Lingoport Dedicated VM Restricted Access to the Repository
The first step in this deployment is to instantiate an AWS VM. The Customer IT adds only that VM to the list of specific IP's which can access the repositories. The only access provided is to version control systems such as Git (GitHub, Bitbucket, Gitlabs), TFS, or Subversion.
No customer data or systems (credit card information, live databases, client data, etc.) are granted access to the Lingoport Dedicated VM.
Restricted Access to the Lingoport Dedicated VM
Conversely, only a restricted set of IP's are allowed to access the Lingoport Dedicated VM. For instance, a system has to be either in the Customer's network or in the Lingoport network to be granted access to the Lingoport Dedicated VM. It behaves as an extension of the customer's network. No other party can gain access to the Lingoport Dedicated VM.
Furthermore, access to the AWS Lingoport Dedicated VM is restricted by SSH key. A public key needs to be set on the Dedicated VM to access connections.
HTTPS and IP Restrictions to the Lingoport Applications
The application on the AWS Lingoport Dedicated VM (the Dashboard or Jenkins) is only accessible when the following conditions are met:
The IP of the calling system is granted access, typically:
- Customer IP range
- Lingoport IP range
The application is secured by account and password over HTTPS.
In other words:
- No one outside the authorized range can reach the system
- Only authorized accounts access / see the Dashboard
- Data communication is over HTTPS
Secure Transfer of Resource Files to/from Translation
The AWS Lingoport Dedicated VM has code obtained from the repositories on the customer's version control system. A few files, those which require translations, need to be sent to a translation group (See Language Service Providers, TMS, etc.). Those application files are called 'Resource Files'. They are not the code of the application, they are the user visible strings. The resource files are typically .properties, .json, .resx, etc. They are not .java, .js, .c#, etc.
Most commonly, in order to secure the send the resource files to and from the translation group, the files transfer over Secure FTP:
- LRM (Lingoport automation) deposits the files on an SFTP endpoint
- The Translation group retrieves the files. They are not on the SFTP any longer
- The Translation group pushes the translated files to another SFTP endpoint.
- LRM (Lingoport automation) retrieves the files from that end point. The files are not the SFTP any longer.
Transfer security:
- The protocol used is Secure FTP (SFTP). Or with specifical allowance and request FTPS.
- The SFTP/FTPS server only allows the minimum IP range necessary:
- Dedicated VM IP range
- Translation Group IP range
- The protocol is SSH (SFTP - Recommended) or SSL (FTPS - as a fallback where specifically requested).
For specific translation vendors, direct connections to the vendor API point may be substituted for SFTP. These connections are encrypted over HTTPS(TLSv1.2), using an api token to authenticate.