Difference between revisions of "Security Strategy"
(→Overview) |
(→FAQ) |
||
| (40 intermediate revisions by 3 users not shown) | |||
| Line 4: | Line 4: | ||
==Overview== |
==Overview== |
||
| − | The Lingoport Suite components (LRM and Globalyzer) need to be secure as well as the system or virtual machine that the components reside on. |
||
| − | |||
| − | If Lingoport's https://www.globalyzer.com is hosting the rulesets, access needs to be considered. |
||
Lingoport works to provide customers with a reliable service that safeguards private information. We implement various security-centric policies in support of these principles. Lingoport’s security standards have been built to support the security conscious, including customers in industries such as Human Resources, Finance, and Medical Systems. |
Lingoport works to provide customers with a reliable service that safeguards private information. We implement various security-centric policies in support of these principles. Lingoport’s security standards have been built to support the security conscious, including customers in industries such as Human Resources, Finance, and Medical Systems. |
||
* We protect our organization, and our customers, by addressing [[Lingoport_Security_Overview#Key Security Principles|Key Security Principles]] |
* We protect our organization, and our customers, by addressing [[Lingoport_Security_Overview#Key Security Principles|Key Security Principles]] |
||
| − | * We consider security [[#Security Throughout Lingoport|Throughout Our Organization]]. |
+ | * We consider security [[Lingoport_Security_Overview#Security Throughout Lingoport|Throughout Our Organization]]. |
| − | * We take customer security very seriously during [[#Security and Service Projects|Service Projects]]. |
+ | * We take customer security very seriously during [[Lingoport_Security_Overview#Security and Service Projects|Service Projects]]. |
| − | * We minimize security exposure to our customers through [[#Security and the Development Process|Security Conscious Product Design]]. |
+ | * We minimize security exposure to our customers through [[Lingoport_Security_Overview#Security and the Development Process|Security Conscious Product Design]]. |
| + | * We adhere to standard security practices in our cloud hosted environments. [[Lingoport_Security_Overview#Security and Cloud Offerings|Security and Cloud Offerings]] |
||
| − | For more details on any of these, please see [[Lingoport Security Overview]] |
+ | For more details on any of these, please see [[Lingoport Security Overview]]. |
| − | ==Lingoport Suite |
+ | == Typical Deployment of the Lingoport Suite and Ports == |
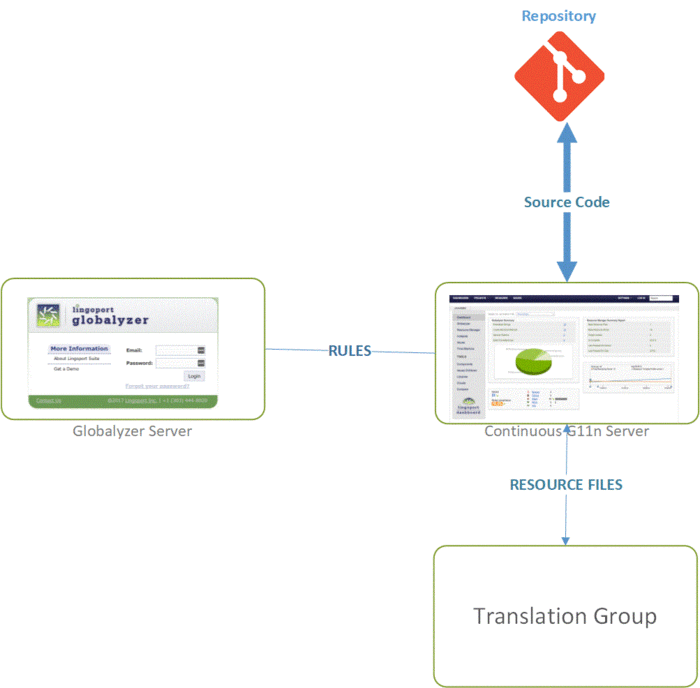
| + | Setting up the Lingoport Suite on a customer's system can be done in many ways. The following is a generalized diagram to show the necessary access to the system. The central system is the Continuous Globalization Server which has the Lingoport Products installed on it and accesses those products and their reports using Jenkins and the Lingoport Dashboard. |
||
| − | *[[Deployment and Security]] |
||
| − | *[[Lingoport Suite Product Security]] |
||
| − | **[https://wiki.jenkins.io/display/JENKINS/Securing+Jenkins Securing Jenkins] |
||
| + | * The code repository needs to be able to read and write from the Continuous Globalization Server. This is done through the Jenkins jobs and Lingobot. The code repository contains the code to be scanned by Globalyzer for localization issues and the resource files to be sent and returned from translation. |
||
| − | ==Lingoport Virtual Machine== |
||
| + | * The Continuous Globalization Server accesses the Globalyzer rulesets that are located either on our hosted server or on a local server. Several security enhancements have been implemented for the Lingoport Globalyzer Server. |
||
| − | [[AWS Security]] |
||
| + | **All passwords are salted and hashed. |
||
| + | **Globalyzer server passwords are encrypted via the bcrypt encryption algorithm. |
||
| + | **Forgot password performs a password reset rather than a retrieval. |
||
| + | **We guard against clickjacking and directory/path traversal attacks. |
||
| + | **Alternatively, the rulesets can be located in the repo or on the Continuous Globalization Server, eliminating the need for the Globalyzer Server. |
||
| + | * The Continuous Globalization Server needs to be able to send and receive resource files with the Translation Management System or Machine Translation Engine (not Lingoport managed). |
||
| + | ** Files will be sent encrypted in transit (typically either SSH or HTTPS using TLS v1.2+) |
||
| + | * Additionally, there are administrative needs for the Continuous Globalization Server to be able to access Jenkins plugins, SMTP email, and SSH access. |
||
| + | [[File:Deployment - Wiki.gif|700px]] |
||
| − | ==More...== |
||
| + | |||
| − | Should we have something that talks about the security enhancements that we have in our products or is this already in these pages? |
||
| + | === Ports === |
||
| − | |||
| + | |||
| − | Several security enhancements have been implemented for the Globalyzer Server. Our password encryption algorithm has been upgraded to use bcrypt, forgot password now performs a password reset rather than retrieval, and we now guard against clickjacking and directory/path traversal attacks. Our version of Tomcat has been upgraded to enable some of these security features. |
||
| + | Please refer to [[Deployment_Scenarios#External_Access_and_Ports]] |
||
| + | |||
| + | === Other aspects === |
||
| + | * Jenkins installation requires access to the Jenkins update site, http://updates.jenkins-ci.org |
||
| + | **[https://wiki.jenkins.io/display/JENKINS/Securing+Jenkins Securing Jenkins] |
||
| + | * Notifications are sent using an SMTP account: The system must allow access to an SMTP server (e.g. smtp.yourcompany.com) |
||
| + | * The Continuous Globalization Server can be deployed in the Cloud using an Amazon AWS virtual system. For more detail on this option please see [[AWS Security]]. |
||
| + | ** Hosted by Lingoport |
||
| + | ** Hosted by the Customer (from a Lingoport provided AMI base image) |
||
== FAQ == |
== FAQ == |
||
| − | Can other customers see our rulesets and information on Globalyzer.com ? |
+ | ===Can other customers see our rulesets and information on Globalyzer.com ? === |
| + | No. Each company is set up with an administrator and users. There is no way for another company member (administrator or member) to access or modify your rulesests. |
||
| + | === Does Lingoport perform vulnerability scans against the software? === |
||
| − | How often is security testing done on the code or the systems? |
||
| + | Yes. |
||
| + | At the application level, Lingoport performs security aware software review both by developer led PR review and automated security analysis against our codebases. |
||
| − | Is data transferred between the customer and the Continuous Globalization System securely? What about between the Continuous Globalization System and the translation vendors? |
||
| + | At a system level, lingoport performs vulnerability scans against our deployed software to provide an additional check for vulnerabilities on top of the code based review process. |
||
| − | How do you document security for third-party applications? |
||
| + | ===Is data transferred between the customer and the Continuous Globalization System securely? === |
||
| − | For Services customers, how do you ensure that the code and company information is secure? |
||
| + | Yes. Lingoport hosted systems are always HTTPS with the latest encryption standards from LetsEncrypt. Data transfer is performed over HTTPS and SSH. |
||
| − | How are security issues and concerns handled within the company? |
||
| + | Customers may also elect to host most or all Lingoport software on premise, in which case information transfer may be kept internal to the Customer's network using Customer managed HTTPS certificates and configuration. |
||
| − | How does Lingoport monitor an AWS VM for security issues ( logins, invalid logins, data transfers, etc)? |
||
| + | ===Is data transferred between the Continuous Globalization System and the translation vendors? === |
||
| − | Has Lingoport had any security breaches? |
||
| + | Lingoport's Localyzer automates translation for software. Localyzer will send translation content to the customer's selected translation vendor. This translation content will constitute partial or whole resource files, which contain lists of English or translated strings that are displayed in the application. |
||
| + | The transfer target will depend on the translation vendor chosen by the customer. |
||
| + | |||
| + | Most common are: |
||
| + | * A customer managed SFTP server |
||
| + | ** Lingoport also provides the option to host an SFTP server if preferable to the customer. |
||
| + | * For some translation vendors, API calls may be performed over HTTPS. |
||
| + | |||
| + | ===For Services customers, how do you ensure that the code and company information is secure?=== |
||
| + | Lingoport works closely with customers to ensure the best security protocol. We want to make sure that the customer is comfortable and confident letting us work with their code. For services engagements, Lingoport must access to source code repositories which are in scope for internationalization analysis and refactoring per service contract with Lingoport. Other customer data is not needed to perform our service engagements. |
||
| + | |||
| + | * Lingoport can obtain secured laptops for authorized Lingoport Services personnel with access to the company's repositories |
||
| + | * Lingoport has also worked with special VPN access to the code repositories |
||
| + | |||
| + | ===How are security issues and concerns handled within the company? === |
||
| + | Security issues are dealt with as soon as detected and then become part of our ongoing security tests. |
||
| + | |||
| + | To ensure that issues are not missed, processes are in place to raise detected issues, assign them, and track them through resolution. |
||
| + | |||
| + | ===How does Lingoport monitor an AWS VM for security issues ( logins, invalid logins, data transfers, etc)? === |
||
| + | |||
| + | Comprehensive system logs are maintained and secured for all systems. Logs are reviewed for suspicious events. |
||
| + | |||
| + | ===Has Lingoport had any security breaches? === |
||
| + | Yes on external test systems. Those have been remedied in a timely fashion and did not affect any of our customers or our internal system. Our security has been reinforced based on this breach. |
||
| + | |||
| + | === Where do I send my security concerns? === |
||
Please send any security inquiries or reports to either support@lingoport.com or security@lingoport.com. |
Please send any security inquiries or reports to either support@lingoport.com or security@lingoport.com. |
||
| + | === What encryption protocols are in place? === |
||
| − | Globalyzer supports the additional security of HTTPS for all data that passes between the Client and the globalyzer.com Server. |
||
| + | |||
| + | ==== HTTPS traffic (lingoport hosted sytems) ==== |
||
| + | |||
| + | For systems that Lingoport hosts and controls, HTTPS is encrypted over TLS Version 1.2 or greater. Specific config options are based on LetsEncrypt defaults: |
||
| + | <nowiki> |
||
| + | SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 |
||
| + | SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384</nowiki> |
||
| + | |||
| + | ==== SSH ==== |
||
| + | |||
| + | A typical SSH encryption configuration used at Lingoport would be: |
||
| + | |||
| + | <nowiki> |
||
| + | gssapikexalgorithms gss-gex-sha1-,gss-group1-sha1-,gss-group14-sha1- |
||
| + | |||
| + | ciphers chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc |
||
| + | |||
| + | macs umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1 |
||
| + | |||
| + | kexalgorithms curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1</nowiki> |
||
| + | |||
| + | ==== Disk Encryption ==== |
||
| + | |||
| + | Lingoport uses AWS for hosted servers. We use EBS encryption (AES-256) using an AWS managed key. |
||
| + | |||
| + | ==== Password encryption ==== |
||
| + | |||
| + | All user passwords are hashed and salted before storage in any Lingoport application database. |
||
| + | |||
| + | Most lingoport software, such as the Globalyzer Server, uses bcrypt for encrypting user passwords. |
||
| + | |||
| + | One exception is that Lingoport makes extensive use of SonarQube as a software base. SonarQube salts user passwords, and then hashes them using SHA1. |
||
| + | |||
| + | ==== General Encryption ==== |
||
| + | |||
| + | Lingoport Localyzer encrypts some sensitive data via AES-128. |
||
| + | Lingoport uses Jenkins, which employs AES-128-ECB[https://web.archive.org/web/20190916195518/http://xn--thibaud-dya.fr/jenkins_credentials.html|source]. |
||
| − | L10n Vendor Lingoport FTP Protocol: FTP supports SSH and SSL encryption; The FTP system can allow only some IP ranges to access the FTP port(s) |
||
| + | The Lingoport Dashboard (SonarQube server base) may optionally enable AES-128 encryption of some sensitive information on disk. |
||
| − | Machine Learning: to use Machine Learning, you must install H2O.ai to your system. It's an in-memory platform so you don't need to worry about the security of your code and data. |
||
| + | === Does Lingoport support LDAP?=== |
||
| − | LDAP and security. |
||
| + | Globalyzer server, Jenkins, and Dashboard support LDAP. Other components do not need LDAP. |
||
Latest revision as of 22:11, 24 August 2022
Contents
- 1 Overview
- 2 Typical Deployment of the Lingoport Suite and Ports
- 3 FAQ
- 3.1 Can other customers see our rulesets and information on Globalyzer.com ?
- 3.2 Does Lingoport perform vulnerability scans against the software?
- 3.3 Is data transferred between the customer and the Continuous Globalization System securely?
- 3.4 Is data transferred between the Continuous Globalization System and the translation vendors?
- 3.5 For Services customers, how do you ensure that the code and company information is secure?
- 3.6 How are security issues and concerns handled within the company?
- 3.7 How does Lingoport monitor an AWS VM for security issues ( logins, invalid logins, data transfers, etc)?
- 3.8 Has Lingoport had any security breaches?
- 3.9 Where do I send my security concerns?
- 3.10 What encryption protocols are in place?
- 3.11 Does Lingoport support LDAP?
Overview
Lingoport works to provide customers with a reliable service that safeguards private information. We implement various security-centric policies in support of these principles. Lingoport’s security standards have been built to support the security conscious, including customers in industries such as Human Resources, Finance, and Medical Systems.
- We protect our organization, and our customers, by addressing Key Security Principles
- We consider security Throughout Our Organization.
- We take customer security very seriously during Service Projects.
- We minimize security exposure to our customers through Security Conscious Product Design.
- We adhere to standard security practices in our cloud hosted environments. Security and Cloud Offerings
For more details on any of these, please see Lingoport Security Overview.
Typical Deployment of the Lingoport Suite and Ports
Setting up the Lingoport Suite on a customer's system can be done in many ways. The following is a generalized diagram to show the necessary access to the system. The central system is the Continuous Globalization Server which has the Lingoport Products installed on it and accesses those products and their reports using Jenkins and the Lingoport Dashboard.
- The code repository needs to be able to read and write from the Continuous Globalization Server. This is done through the Jenkins jobs and Lingobot. The code repository contains the code to be scanned by Globalyzer for localization issues and the resource files to be sent and returned from translation.
- The Continuous Globalization Server accesses the Globalyzer rulesets that are located either on our hosted server or on a local server. Several security enhancements have been implemented for the Lingoport Globalyzer Server.
- All passwords are salted and hashed.
- Globalyzer server passwords are encrypted via the bcrypt encryption algorithm.
- Forgot password performs a password reset rather than a retrieval.
- We guard against clickjacking and directory/path traversal attacks.
- Alternatively, the rulesets can be located in the repo or on the Continuous Globalization Server, eliminating the need for the Globalyzer Server.
- The Continuous Globalization Server needs to be able to send and receive resource files with the Translation Management System or Machine Translation Engine (not Lingoport managed).
- Files will be sent encrypted in transit (typically either SSH or HTTPS using TLS v1.2+)
- Additionally, there are administrative needs for the Continuous Globalization Server to be able to access Jenkins plugins, SMTP email, and SSH access.
Ports
Please refer to Deployment_Scenarios#External_Access_and_Ports
Other aspects
- Jenkins installation requires access to the Jenkins update site, http://updates.jenkins-ci.org
- Notifications are sent using an SMTP account: The system must allow access to an SMTP server (e.g. smtp.yourcompany.com)
- The Continuous Globalization Server can be deployed in the Cloud using an Amazon AWS virtual system. For more detail on this option please see AWS Security.
- Hosted by Lingoport
- Hosted by the Customer (from a Lingoport provided AMI base image)
FAQ
Can other customers see our rulesets and information on Globalyzer.com ?
No. Each company is set up with an administrator and users. There is no way for another company member (administrator or member) to access or modify your rulesests.
Does Lingoport perform vulnerability scans against the software?
Yes.
At the application level, Lingoport performs security aware software review both by developer led PR review and automated security analysis against our codebases.
At a system level, lingoport performs vulnerability scans against our deployed software to provide an additional check for vulnerabilities on top of the code based review process.
Is data transferred between the customer and the Continuous Globalization System securely?
Yes. Lingoport hosted systems are always HTTPS with the latest encryption standards from LetsEncrypt. Data transfer is performed over HTTPS and SSH.
Customers may also elect to host most or all Lingoport software on premise, in which case information transfer may be kept internal to the Customer's network using Customer managed HTTPS certificates and configuration.
Is data transferred between the Continuous Globalization System and the translation vendors?
Lingoport's Localyzer automates translation for software. Localyzer will send translation content to the customer's selected translation vendor. This translation content will constitute partial or whole resource files, which contain lists of English or translated strings that are displayed in the application.
The transfer target will depend on the translation vendor chosen by the customer.
Most common are:
- A customer managed SFTP server
- Lingoport also provides the option to host an SFTP server if preferable to the customer.
- For some translation vendors, API calls may be performed over HTTPS.
For Services customers, how do you ensure that the code and company information is secure?
Lingoport works closely with customers to ensure the best security protocol. We want to make sure that the customer is comfortable and confident letting us work with their code. For services engagements, Lingoport must access to source code repositories which are in scope for internationalization analysis and refactoring per service contract with Lingoport. Other customer data is not needed to perform our service engagements.
- Lingoport can obtain secured laptops for authorized Lingoport Services personnel with access to the company's repositories
- Lingoport has also worked with special VPN access to the code repositories
How are security issues and concerns handled within the company?
Security issues are dealt with as soon as detected and then become part of our ongoing security tests.
To ensure that issues are not missed, processes are in place to raise detected issues, assign them, and track them through resolution.
How does Lingoport monitor an AWS VM for security issues ( logins, invalid logins, data transfers, etc)?
Comprehensive system logs are maintained and secured for all systems. Logs are reviewed for suspicious events.
Has Lingoport had any security breaches?
Yes on external test systems. Those have been remedied in a timely fashion and did not affect any of our customers or our internal system. Our security has been reinforced based on this breach.
Where do I send my security concerns?
Please send any security inquiries or reports to either support@lingoport.com or security@lingoport.com.
What encryption protocols are in place?
HTTPS traffic (lingoport hosted sytems)
For systems that Lingoport hosts and controls, HTTPS is encrypted over TLS Version 1.2 or greater. Specific config options are based on LetsEncrypt defaults:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
SSH
A typical SSH encryption configuration used at Lingoport would be:
gssapikexalgorithms gss-gex-sha1-,gss-group1-sha1-,gss-group14-sha1- ciphers chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc macs umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1 kexalgorithms curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
Disk Encryption
Lingoport uses AWS for hosted servers. We use EBS encryption (AES-256) using an AWS managed key.
Password encryption
All user passwords are hashed and salted before storage in any Lingoport application database.
Most lingoport software, such as the Globalyzer Server, uses bcrypt for encrypting user passwords.
One exception is that Lingoport makes extensive use of SonarQube as a software base. SonarQube salts user passwords, and then hashes them using SHA1.
General Encryption
Lingoport Localyzer encrypts some sensitive data via AES-128.
Lingoport uses Jenkins, which employs AES-128-ECB[1].
The Lingoport Dashboard (SonarQube server base) may optionally enable AES-128 encryption of some sensitive information on disk.
Does Lingoport support LDAP?
Globalyzer server, Jenkins, and Dashboard support LDAP. Other components do not need LDAP.